This article will discuss setting up Cisco Anyconnect with LDAP/Domain Authentication. I will be showing both the ASDM/GUI and CLI commands. I recommend the GUI method once, then use the CLI once you understand it.
This post describes the procedure to configure a Cisco ASA firewall with LDAP authentication for AnyConnect Remote Access VPN access. Refer to the previous posts for configuring AnyConnect Remote Access VPNs. ASA AnyConnect IKEv2/IPSec VPNASA AnyConnect SSL-VPNASA Split Tunneling Active Directory Pre-requisites The following pre-requisites for Active Directory are required. We have bought ASA 5506-x. Now we need to implement Active Directory Integration. So we need Sourcefire User Agent. How can I download it? Examples of LDAP servers that the Cisco ASA can operate with include Microsoft Active Directory, OpenLDAP, and Novell. Note: You may be aware that the Microsoft Active Directory (and other LDAP servers) can be integrated with the Cisco Secure ACS or ISE as external identity stores.
Replace the following below with your own:
You will also need the following NAT Rules to facilitate communication between local and client VPN subnets.
The only thing you won’t see in here is configuring an A record or the SSL cert for the client VPN.
Now here’s how to do all of this from the GUI/ASDM.
Let’s first create the NAT rule necessary to facilitate communication with our LAN and the Client VPN subnet.
Here are the network objects and NAT rule.
Configuration > Firewall > objects > network objects
Configuration > Firewall > NAT Rules
Here is the order of the NAT Rules.
Ok, now go get the latest anyconnect .pkg for Windows from Cisco.com
Great now let’s go back into ASDM so we can configure Anyconnect.
Head over to the configuration, Remote Access VPN tab. Then enable the following:
Check “Allow Access” on outside
“Bypass interface access…”
Also, select the “enable cisco anyconnect VPN…” and upload the .pkg image we downloaded. Do this by clicking yes to the prompt about designating the anyconnect image. Then Upload your image, finally click okay once it’s autoselected.
Now head over to the AAA column menu
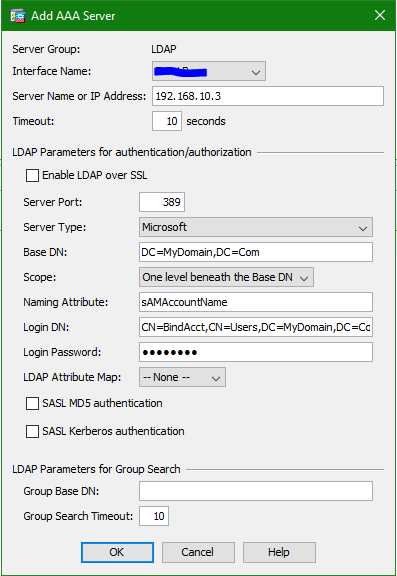
We first need to create the LDAP server group and attribute MAP for our connection profile.
Click “Add”
Set it to the following
Click ok and then click “add” in the bottom server group tab
Fill out the following page, don’t forget to create a service account for the ASA. Of course replace the IP with your AD server’s IP.
Don’t forget to test your server, click Test which is the last item in the right column and enter domain creds to test.
You should see a success.
Now click the LDAP MAP Attribute bar
It will expand the window, now click add
Name it “anyconnectLDAP” set the attribute to memberOf and the Cisco attribute to GroupPolicy and click add.
Then head over to the mapping of attribute value tab and click add
Put the FULL DN of the AD group that will have remote VPN users in it. Make sure to not nest groups in there. Here’s the DN I used.
CN=RemoteUsers,CN=Users,DC=SDC,DC=Local
Then set the cisco attribute to “RemoteUsers”. Doing this means that any user of that group gets assigned the group policy of “RemoteUsers” which we will create later. Finally click “Add” then “OK”.
Asa Active Directory Integration Definition
Then click ok to the final window.
Now go back, edit your LDAP server group, and set the LDAP attribute MAP that we just created as the one for that server group.
Side tangent:
Also, here’s a screenshot of the group and user I used for the LDAP connection and attribute map.
If you are not familiar with distinguished names, I suggest you enable advanced views in dsa.msc and then go into the attributes of your object, the distinguished name will be there. Here’s how to do that.
Dsa.msc > views > advanced features
Then browse to the object properties > attribute editor > find distinguished name
Ok back to the ASA config.
Now head over to the Group Policies Tab and click Add.
Name the GP “RemoteUsers” remember this is going to be assigned via the LDAP attribute map. Also set the following settings. NOTE IT’S VERY IMPORTANT TO SET A SIMULTANEOUS LOGIN!
Then click OK to close out the menu. Now we need to create a GP named “NOACCESS” with the following settings (0 simultaneous users)
Click Ok to save that too.
Now head over to connection profiles and add a new profile
Create a profile, preferably one with a name/alias your users will recognize.
Be sure to select the AAA group created earlier, set the internal DNS and set the GP to “NOACCESS”. The LDAP attribute map we created earlier will dynamically assign the GP when the user logins. Also set the subnet/dhcp settings that you want.
After saving the profile, it should auto enable. Make sure to check the box in the original window to allow users to select their own profile. (helpful later if you setup multiple profiles, or webvpn)
An important, and usually implemented feature of client VPN solutions is split tunneling. This feature lets you choose what traffic should and should not go over the tunnel. If we don’t configure this ALL traffic goes through the client VPN. This can severely impact the environment if there isn’t enough bandwidth available.
Now let’s go back to the “Remote Users” group policy we created. Edit the policy, and go to the “split-tunneling” menu.
See the network list I just unchecked? Click “Manage” to the right of that and create a standard ACL. Then add the subnets that client VPN users will access over the VPN.
After clicking OK
After closing that menu
Now click OK in the last window to close all of that out.
Finally let’s setup HTTP to HTTPS redirection so that when users browse they will be redirected.
Configuration > Device management > Advanced > HTTP Redirect > highlight Outside interface > click edit > check redirect checkbox > click ok > Apply settings
Ok we’re all done! Let’s test it now! I’m doing this all from a virtual lab with a simulated WAN.
Looks like it worked because I was asked to download the anyconnect package.
Let’s install the client.
Now since we don’t have a publicly trusted SSL cert, we are using the default self signed one. So we need to go into anyconnect to uncheck the “block” box below to allow us to connect.
Now let’s connect.
Notice the SSL error, just click continue.
Ok now let’s authenticate with LDAP
Looks like it accepted.
Don’t forget to verify that the split tunnel is working
Awesome!
Troubleshooting
If for whatever reason LDAP auth failed, use the following debug commands to figure out what went wrong in the ASA.
Debug ldap 255
Debug aaa common 255
The biggest issue I see with the above is something with domain auth not working properly. Then the user is denied a login because the default group policy is NOACCESS. Then I see people just edit the noaccess policy to allow users in, I HATE THAT. Check the distinguished names, make sure the DN isn’t too long (some versions hate that). Use the freaking debugs. The LDAP group should be translated via the attribute map to a proper group policy, you can verify if it’s not via the debug.
Integrating biometric authentication with Active Directory can be a simple process. If you already use Azure Active Directory, it’s as simple as using the built-in MFA. If you’re not using Azure, there are other options, like Okta, that we recommend. Here’s a guide.
What is biometric authentication?
Biometric authentication refers to fingerprints, facial recognition, voice recognition, and other elements users can utilize to authenticate their identity. Frequently, biometric authentication is used as a second authentication tool. For example, a user may enter a password and then be prompted to submit a fingerprint as a second proof of identity. In some cases, biometric authentication can be faster and more “friction-less” than more conventional authentication factors.
How do I deploy biometric authentication in Windows Active Directory?
There are a variety of ways to deploy biometric authentication for Windows Active Directory. For example, if you’re looking for fingerprint authentication across Windows devices, Microsoft makes this possible via Windows Hello. Windows Hello takes advantage of Mobile Device cameras and fingerprint readers, and laptops with fingerprint readers.
For proven biometric authentication across all devices and operating systems, we look to products like Okta. Okta provides single-sign on, and can be configured to allow fingerprint authentication with various APIs or add-ons, like Imprivata.
How do I deploy biometric authentication in Windows Active Directory using Azure?
Microsoft Azure makes fingerprint biometric authentication easy by allowing administrators to select the option within the Group Policy options (Computer Configuration > Policies). There are three kinds of deployment: On-Premise Deployment, Hybrid Deployment, and Cloud Deployment.
Can I deploy facial recognition or voice authentication in Windows Active Directory using Azure?
Yes, Microsoft offers FIDO2 security keys, which support biometric authentication, including facial recognition, to Azure Active Directory, Per Microsoft:
“Using a FIDO2 security key, the Microsoft Authenticator app, or Windows Hello, all Azure AD users can now sign in without using a password.
These strong authentication factors are based off the same world class, public key/private key encryption standards and protocols, which are protected by a biometric factor (fingerprint or facial recognition) or a PIN. Users apply the biometric factor or PIN to unlock the private key stored securely on the device. The key is then used to prove who the user and the device are to the service.
In addition, to help you get started on your own passwordless journey, we’re rolling out new public preview capabilities, including: 1) A new Authentication methods blade in your Azure AD admin portal that allows you to assign passwordless credentials using FIDO2 security keys and passwordless sign-in with Microsoft Authenticator to users and groups; 2) Updated capabilities in the converged Registration portal for your users to create and manage FIDO2 security keys; 3) Ability to use FIDO2 security keys to authenticate across Azure AD-joined Windows 10 devices on the latest versions of Edge and Firefox browsers.”
Can I integrate biometric authentication with Active Directory if we don’t use Azure?
Yes. You can integrate biometric authentication with Active Directory with non-Azure cloud data centers via Okta, Idaptive, and other IAM solutions. For example, Okta offers thousands of pre-integrated applications for immediate use, including biometric authentication options. Then, Okta makes management seamless, plus:
“[Okta] enables delegation of continuous monitoring, reporting, and management. Any changes or updates to a user will synchronize their access policies in real-time while maintaining an audit trail. This way, IT teams can easily generate accurate reports on user status and health.”
Do I need a Biometric Authentication consultant near me?
The most important factor is experience and effective workflow, whether in-person, on-site, virtual, or off-site. That said, we think working with a biometric authentication consultant near you is an advantage. This will allow your consultant to better communicate with existing IT teams, and better understand your current information architecture. A non-local consultant becomes a good option if they follow security best practices, and have an established virtual workflow. Why? Location is less significant when virtual workforce tools are effectively adopted by consultant and client, whether a small business or global enterprise. Plus, on-site specialists can become costly. Bottomline, look for a biometric authentication consultant who offers an excellent communication process, clear workflow, and custom security solution for your business.
Have questions about finding an
Biometric Authentication consultant?
Asa Active Directory Integration Examples
Call (925) 918-6618 the consultation is free.
About Sennovate
Asa Active Directory Authentication Vpn
Sennovate delivers custom identity and access management solutions to businesses around the world. With global partners and a library of 1000+ integrations, we implement world-class cybersecurity solutions that save your company time and money. We offer a seamless experience with integration across all cloud applications, and a single price for product, implementation, and support. Have questions? The consultation is always free. Email [email protected] or call us at: (925) 918-6618
