Every internet router comes with a user name and password to gain access to its configuration pages. You don’t want just anyone on the network being able to edit things like firewall settings or the WiFi password. Users are normally advised to change the password for security reasons but many still don’t do that or even know it’s advisable to.
Today you'll be able to download a collection of passwords and wordlist dictionaries for cracking in Kali Linux. A wordlist or a password dictionary is a collection of passwords stored in plain text.
- 👍 Awesome password to hack. Contribute to j3ers3/PassList development by creating an account on GitHub.
- The file “passlist.txt” contains a list of usernames and passwords in two columns. Each row in the list will be inserted into the net use command. C208B Grand Caravan HD For X-Plane 10 Serial Keyl Kcdw Crack Keygen Serial 27l List Of New Vegas Companionsl.
Forgetting your own or the default router password is very common because you don’t really need to access the router settings very often. However, it is quite troublesome when you don’t know the router password because there are several important settings that could literally block you and others from accessing the network or internet completely.
Aircrack-ng handshake.cap -w /path/to/wordlist.txt I've personally tried it and was able to crack 3/10 wifi networks near me. Just bare in mind that using password cracking tools takes a lot of time, especially if done on a computer without a powerful GPU. Useful lists for geeks, machine learning, and linguists. Download: rockyou.txt Copyright © ScrapMaker.com 2008-2020. All rights reserved.
The most obvious advice you’d find on the Internet is to simply reset the router back to the default configuration. That is not a foolproof method because you still need to know the default password. Here are some ways to access your router if you’ve forgotten or don’t know the password.
Find The Default Router Username And Password
Many computer users don’t bother changing the router username and password so it may still be set at the manufacturer or internet provider defaults. If you’re pretty sure the router password hasn’t been changed, there are a couple of things you can do.
1. Find The Router Password Online
A simple solution to try is searching for your router’s default password online. Using a search engine will bring up something but an easier way is checking at an online database for router passwords. Here are three websites you can check.
- PortForward.com
- PCWinTech.com A-L | M-Z
- RouterPasswords.com
At the very least, you will need to know the manufacturer of the router or the name of the ISP if the router came from your service provider. Knowing the model is also helpful but not essential.
Between them, the three sites above list literally thousands of router models and their default passwords. The chances are very good that the branded model or ISP supplied model is listed on at least one.
2. Check The Router For the Default Password
If you have easy access to the router, simply looking at the bottom or back of it might show the default user name and password to get into the router.
Many routers will either have the password printed somewhere on them or a small removable plastic card which might also contain default WiFi login details on the other side.
3. Guess The Default Password
If you’re unlucky enough that your router isn’t listed on the databases above or there’s nothing on the router itself, here are a few usernames:passwords that are very common. You can also try combinations between any of the below.
admin:admin
admin:password
admin:1234
admin:[blank]
[blank]:admin
root:root
root:password
Many Netgear routers default to admin:password|1234, several Zyxel routers use a combination of [blank]|root|admin:1234, while D-Link routers often use admin:admin|[blank]. Virtually all TP-Link routers use the same combination of admin:admin.
Try To Crack The Router Password
This method will simply try to find the router password by making multiple attempts to log in to your router with different credentials each time. This may not work if your router has built in protection against multiple failed login attempts.
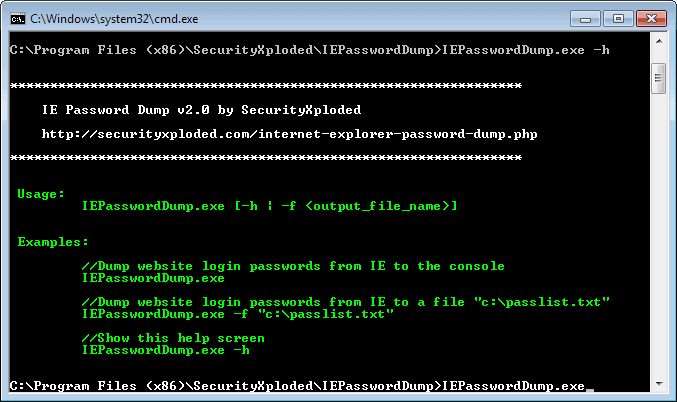
4. Router Password Kracker
Router Password Kracker from Security Xploded tries to recover the forgotten router password through a dictionary attack. This means it works based on a list of words found in a dictionary file. The program itself comes with a password list (passlist.txt) which contains just over 3,000 common or router related words.
Enter the IP address of the router, common addresses are 192.168.0.1 or 192.168.1.1. A drawback of this method is you have to know or have a good idea of what the user name is. If you have no idea, common names are root, admin, user, or even a blank user name.
The chance of this working is obviously quite slim if you have changed the password to something personal. At least this method is automated and much faster compared to manually trying passwords. We found that the program didn’t work with our router. It could be because our router’s landing page does not ask for a password. If yours is the same, it might not work either.
Download Router Password Kracker
5. Router Password Recovery
This is basically the same tool as Router Password Kracker but instead runs from the command line and doesn’t have a graphical user interface. The syntax is:
RouterPasswordRecovery.exe -i ipaddress -u username -f passlist
Like above, you need to know the username of the router or you can narrow it down to just a few possible options. If you don’t supply a username it will default to using admin.
Download Router Password Recovery
Pass List To Powershell
Note: A dictionary based option to crack a password is only as good as the list of words you are using. In addition to the words in the passlist.txt provided by Security Xploded, you can also add your own passwords to the list if you have some ideas. Be aware that all entries in the list are case sensitive.
Decrypt a Router Configuration File
Most routers allow you to export or save the current configuration settings to a backup file (usually .conf). If you have previously done that and have the backup file to hand, the changed password should be inside but it will be encrypted. Here’s a couple of tools that can try to decrypt the router password.
6. RouterPassView
RouterPassView decrypts the encrypted passwords that are saved in the configuration file from your router. It supports about 30 different brands including names like Netgear, Linksys, D-Link, TP-Link, Edimax, ZTE, and several other generic types of router. Check the RouterPassView webpage for a full list.
If RouterPassView is able to decrypt the password in the router configuration file, the process is instant. It can also decrypt wireless passwords and internet login passwords stored in the configuration file. The tool itself is most likely to work if you have one of the routers in the supported list. However, you can still try if yours isn’t listed. Our router isn’t listed but we still got the login password.
Download RouterPassView
7. Router Password Decryptor
Pass List To Controller
This is another tool by Security Xploded but it works similarly to RouterPassView whereby it tries to decrypt stored passwords in a router configuration file. The program officially supports Cisco, Juniper, DLink, and BSNL routers but there’s also a Smart mode where it will try to decrypt any router’s configuration file.
Browse for the config file or drop it onto the window. Select the router brand from the drop down menu or Smart Mode if the router is not one of the four listed. Then press Start Recovery. In addition to router login passwords, the program can also decrypt WiFi passwords and internet login/PPPoE passwords. Right clicking on a password will offer to copy it to the clipboard or you can export all data to an HTML report.
Download Router Password Decryptor
If All Else Fails…
If none of the options above work, you’re probably left with the last option which is to reset the router back to its default settings.
8. Resetting The Router
Resetting the router back to factory settings will revert everything back to the defaults like when you first received it. This probably won’t cause users with ISP supplied routers too much trouble as important settings will be pre-configured already. You might only need to change something like the WiFi password back to the preferred option.
To reset the router, there’s normally a small button that is sometimes recessed with the word reset near it at the back.
Use a pin or bent paperclip to press the button and hold it for at least 10 seconds. Most routers will turn all lights on or flash the lights before rebooting so you know the reset is working. You will, of course, need to know the default username and password for your router to gain access (see the top of the article).
The disadvantage of resetting a router back to factory defaults is if you have lots of custom configuration settings. You might need to reconfigure everything such as internet connection itself, firewall settings, port forwarding, MAC address filtering, and etc. If the option is there, back up your settings next time!
You might also like:
Recover Windows Login Password Online with LoginRecoveryExport and Import Dial-up and VPN Settings in WindowsHow to Create and Access Shared Folders in Windows 75 Ways to Change Windows User Password Without Knowing Current PasswordReset Windows User Account by Removing Forgotten PasswordOMG THANK YOU SO MUCH!
The “RouterPassView” did it for me. Good stuff
I recommend visiting the the site of the guy who authored RouterPassView: nirsoft.net
His name is Nir Sofer and I found his site when I was running a Novell network at a bank. Most of my help calls were in regard to forgotten Windows passwords.
The network ran seamlessly, by the way. I miss Novell and I really appreciate Linux.
Anyway, although Nirsoft had nothing for me at that time (1999?), I downloaded a few of his utilities to play with. Mail password crackers among other utilities that were effective but frivilous in my opinion.
I visited his site several times over the years and it was apparent that the guy was determined and prolific. When Windows 7 came out I was absolutely stunned at over the rights we were giving up when we hit “I Agree”. I read what I was about to agree to as the OS informed me it was installing Skype, an Update I had no interest in. I was told that I would be giving up all my rights to the images and conversations that went thru Skype. The agreement would establish MS as a discrete partner.
So I looked at the words behind a few other ‘I Agree’ buttons and found that Google, Adobe and just about every bit of software I was using included a share clause.
This is where NirSoft came through. There’s not much any of us can do about the eyes and ears on our work but NirSoft’s numerous utilities were invaluable in pulling back the curtain to reveal the who, what and where of our current state of privacy intrusion. They do it a lot of it in real time and as an added bonus, his utilities don’t add bloat or call home. They are portable and they are lean.
I don’t know anything about Nir other than he seems to have put a lot of time into his work and he’s very generous with his product.
Just sayin’.
ReplyHi Raymond . Thanks for the information.
This will definitely be of use and help at times of need.
I have a ZTE F660 router that doesn not have the web configuration tool. I want to reconfigure it to connect to multiple devices in a LAN but i can’t.
I have reset it to default settings but even then am not able to ssh the router from my laptop.
Any help please?
ReplyIt is a very common problem we all face often. hope I will be able to reset my router password if I forget it in future. first three steps are easy compared to the fourth one. if we can solve the problem using any one of the first three steps then it will be okay.
ReplyHi, we bought a second hand WiFi router and the default password does not work, we don’t have the password the previous owners used. How do I reset this, I have tried hard reseting but it doesn’t work. It’s a Duxbury router
Thank you
Replythank you so muvh for the information
ReplyDownload Rom file from 192.168.1.1/rom-0 and then open it using routerpassview , this should work
ReplyThank you very much. It still working and solve my problem forgot my router password.
ReplyThis redirect to admin page. What next??
Replyfolks, I am looking for some help to crack the admin password for BintecX4300 router
Replyhi to every one of all specially thx for ray for letting me know how to reset router all u guys ? all the information i read is useful and keep giving information
Replythx raymond for this information..
i just read it and i think it will help me alot…
ray,
i just heard that you come from Malaysia.
it’s true?
Leave a Reply
Karkinos is a light-weight ‘Swiss Army Knife’ for penetration testing and/or hacking CTF’s.
Currently Karkinos offers the following:
- Encoding/Decoding characters
- Encrypting/Decrypting text or files
- Reverse shell handling
- Cracking and generating hashes
Dependencies
- Any server capable of hosting PHP; tested with Apache Server
- Tested with PHP 7.4.9
- Python3
Make sure it is in your path as:
Windows: python
Linux: python3
If it is not, please change the commands in includes/pid.php - pip3
- Raspberry Pi Zero friendly (crack hashes at your own risk).
Installing
This installation guide assumes you have all the dependencies.
Linux/BSD
- git clone https://github.com/helich0pper/Karkinos.git
- cd Karkinos
- pip3 install -r requirements.txt
- cd wordlists && tar -xf passlist.zip You can also unzip it manually using file explorer if tar is not installed. Just make sure passlist.txt is in wordlists directory.
- Add extension=php_sqlite3.dll to your php.ini file.
If you don’t know where to find this, refer to the PHP docs. - Thats it! Now just host it using your preferred web server or run: php -S 127.0.0.1:8888 in the Karkinos directory.
Important: using port 5555 will conflict with the reverse shell handler server
If you insist on using port 5555, change the reverse shell handler server PORT value in /bin/Server/app.py Line 87
Windows
- git clone https://github.com/helich0pper/Karkinos.git
- cd Karkinos
- pip3 install -r requirements.txt
- cd wordlists && tar -xf passlist.zip
You can also unzip it manually using file explorer if tar is not installed. Just make sure passlist.txt is in wordlists directory. - Add extension=php_sqlite3.dll to your php.ini file.
If you don’t know where to find this, refer to the PHP docs. - Thats it! Now just host it using your preferred web server or run: php -S 127.0.0.1:8888 in the Karkinos directory.
Important: using port 5555 will conflict with the reverse shell handler server
If you insist on using port 5555, change the reverse shell handler server PORT value in /bin/Server/app.py Line 87
Encoding/Decoding
This page allows you to encode/decode in common formats (more may be added soon)
Encrypt/Decrypt
Encrypting and decrypting text or files is made easy and is fully trusted since it is done locally.
Reverse Shell Handling
Reverse shells can be captured and interacted with on this page.
Create a listener instance
Configure the listener
Start the listener and capture a shell
Full reverse shell handling demo:
Generating Hashes
Karkinos can generate commonly used hashes such as:
- MD5
- SHA1
- SHA256
- SHA512
Cracking Hashes
Karkinos offers the option to simultaneously crack hashes using a built-in wordlist consisting of over 15 million common and breached passwords. This list can easily be modified and/or completely replaced.
Disclaimer
By using Karkinos suite to make penetration tests or any hacking CTF’s more efficient. It should be used on applications that you have permission to attack only. Any misuse or damage caused will be solely the users’ responsibility.
